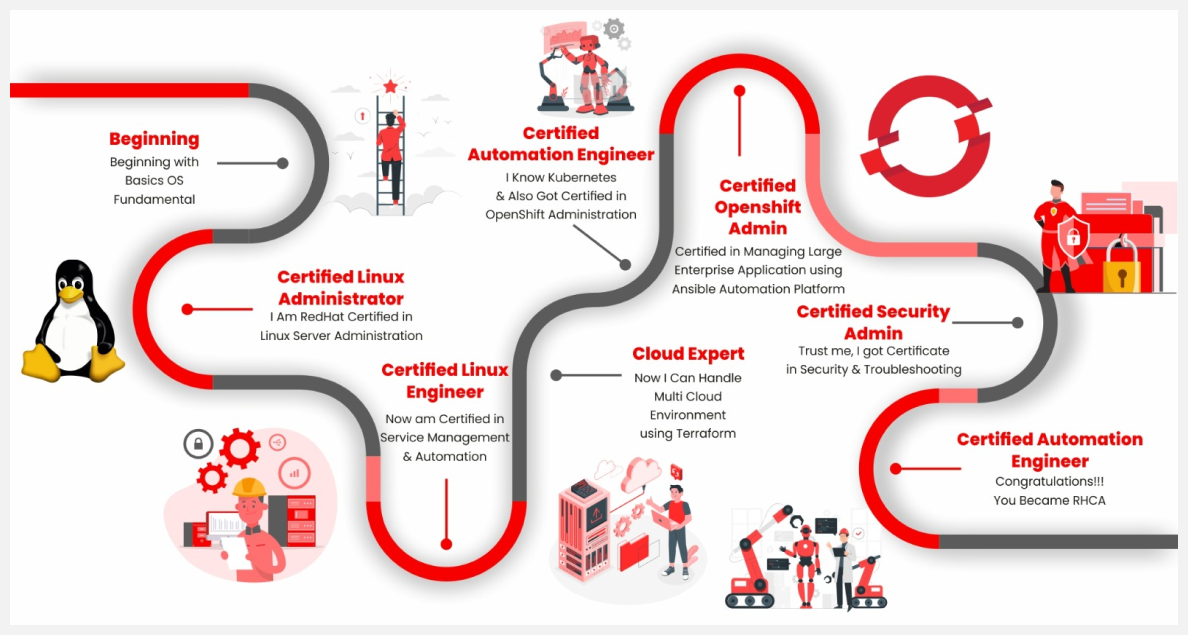
Why Wait? Skip the MCA and Mtech Routes and Dive Straight Into Practical Learning
One of the first things that comes to any aspiring individual mind is whether the intended course is one for them or not. The same question must be twirling inside of your mind too, especially after having already invested so much of your energy, time and money into different courses.
If you wish to check whether you are making it on to the list of the most suitable RHCA candidate or not, here is a check list you can look for –